Featured Post: The Evolution of Ransomware in 2024

Ransomware attacks continue to plague organizations of all sizes. This year has seen a significant shift in tactics, techniques, and procedures (TTPs) employed by ransomware groups. From double extortion to ransomware-as-a-service (RaaS) models, understanding these trends is crucial for effective defense. In this post, we delve into the latest ransomware variants, their targets, and strategies for mitigation.
We will be covering topics such as:
- The rise of new RaaS platforms
- Targeting of critical infrastructure
- Evolution of encryption methods
- Best practices for ransomware prevention and recovery
Read More

Comprehensive Guide to Network Security Audits
Network security audits are essential for maintaining a robust defense against cyber threats. This guide provides a step-by-step approach to conducting thorough network security audits, covering key areas such as vulnerability scanning, penetration testing, and security policy review. Learn how to identify weaknesses in your network infrastructure and implement effective remediation strategies. Authored by Dr. Anya Sharma, Lead Security Consultant at CipherGuard Technologies.
Read More

Understanding and Mitigating Zero-Day Exploits
Zero-day exploits pose a significant threat to organizations, as they target vulnerabilities that are unknown to vendors. This article explores the nature of zero-day exploits, the methods used by attackers to discover and exploit them, and the strategies for mitigating the risk. Discover how techniques like intrusion detection, intrusion prevention, and application whitelisting can help protect your network from zero-day attacks. By Marcus Chen, Senior Security Analyst.
Read More
NetScan Update: Version 3.0 Released with Enhanced Vulnerability Detection
We are excited to announce the release of NetScan version 3.0, featuring significant improvements in vulnerability detection and reporting. This update includes a new scanning engine, support for the latest vulnerability databases, and enhanced reporting capabilities. Upgrade to NetScan 3.0 to benefit from these improvements and stay ahead of emerging threats. This version includes integration with the National Vulnerability Database (NVD) and Common Vulnerabilities and Exposures (CVE) databases.
Read More

Conducting Effective Phishing Attack Simulations for Employee Training
Phishing attacks remain a leading cause of security breaches. This article provides guidance on conducting effective phishing attack simulations to train employees to recognize and avoid phishing attempts. Learn how to design realistic phishing scenarios, track employee performance, and provide targeted training to improve security awareness. Consider using tools like Gophish or KnowBe4 for your simulations. By Emily Carter, Security Awareness Training Specialist.
Read More

Securing the Internet of Things (IoT): Addressing Emerging Security Risks
The proliferation of IoT devices has introduced new security challenges. This post examines the emerging security risks associated with IoT devices, including weak authentication, insecure communication, and lack of updates. Discover best practices for securing IoT devices and protecting your network from IoT-related threats. Experts recommend implementing network segmentation and device monitoring. Written by David Lee, IoT Security Architect.
Read More

Cloud Security Best Practices for 2024 and Beyond
As more organizations migrate to the cloud, ensuring cloud security is paramount. This article outlines cloud security best practices, including data encryption, access control, identity management, and threat detection. Learn how to leverage cloud security tools and services to protect your data and applications in the cloud. Following compliance standards such as SOC 2 and ISO 27001 is crucial. Authored by Sarah Johnson, Cloud Security Engineer.
Read More
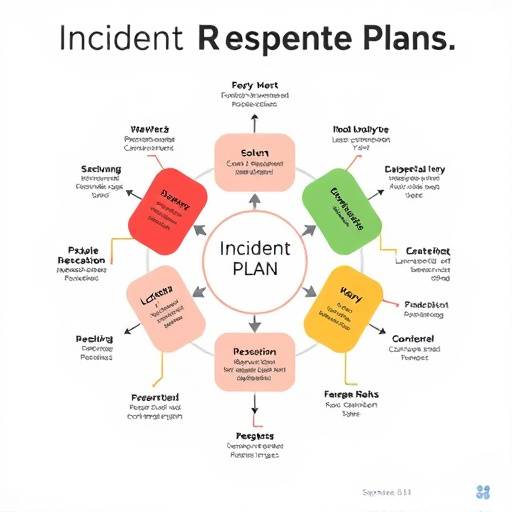
Developing and Implementing an Effective Incident Response Plan
An effective incident response plan is crucial for minimizing the impact of security incidents. This article provides a comprehensive guide to developing and implementing an incident response plan, covering key areas such as incident detection, containment, eradication, recovery, and post-incident analysis. Having a well-defined plan can significantly reduce downtime and data loss. By Michael Rodriguez, Cybersecurity Incident Responder.
Read More

The Evolving Cybersecurity Threat Landscape: Key Trends and Predictions
Staying ahead in cybersecurity requires a deep understanding of the ever-changing threat landscape. This blog post analyzes the key trends shaping the current cybersecurity environment and offers predictions for the future. From AI-powered attacks to increased targeting of cloud infrastructure, we cover the most pressing threats organizations face today. Authored by Elias Thorne, Chief Technology Officer at CipherGuard Technologies.
Read More
"Network security is not a product you buy, it's a process you embrace." - Professor Evelyn Reed, Head of Cybersecurity Department, Stanford Institute of Technology
| Feature | NetScan Basic | NetScan Pro | NetScan Enterprise |
|---|---|---|---|
| Vulnerability Scanning | ✔ | ✔ | ✔ |
| Penetration Testing | ✔ | ✔ | |
| Compliance Reporting | ✔ | ||
| Real-time Threat Detection | ✔ | ✔ | |
| Customizable Reports | ✔ | ✔ |